AWS CloudHSM (Hardware Security Module)
AWS CloudHSM (Hardware Security Module) is a fully managed, single-tenant service designed to manage and secure cryptographic keys. Unlike AWS Key Management Service (KMS), CloudHSM offers complete control of your keys, making it ideal for applications with stringent security and compliance requirements.
CloudHSM is a dedicated hardware security appliance hosted by AWS that enables you to:
- Generate, store, and manage encryption keys.
- Perform cryptographic operations such as encryption, decryption, and signing.
- Retain sole control over keys without AWS having any access.
1. Key Features
- Dedicated Hardware: Each HSM is a physical device provisioned exclusively for your use.
- Compliance:
FIPS 140-2 Level 3certified for enhanced security. Read More - Industry Standard APIs: Supports
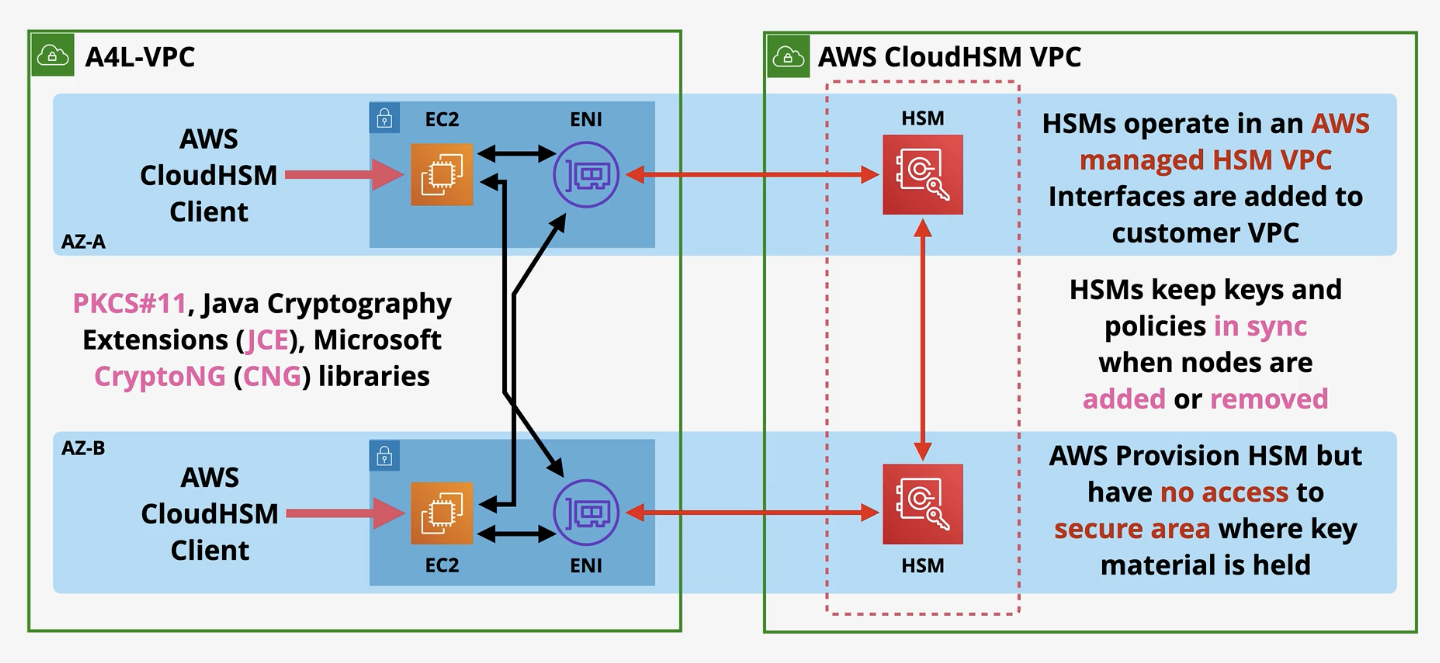
PKCS #11,JCE, andMicrosoft CNGAPIs for seamless integration with third-party applications. - High Availability: HSMs can be clustered across multiple Availability Zones (AZs) for redundancy and resilience.
- No AWS Access: AWS manages the infrastructure but has no access to the secure area where keys are stored.
2. CloudHSM Architecture
- AWS Managed CloudHSM VPC: CloudHSM devices operate in an
isolated AWS-managed VPC. - Customer VPC Integration:
- Elastic Network Interfaces (ENIs) inject the HSM into your VPC for access.
- Applications interact with HSMs via these interfaces.
- High Availability:
- Deploy at least two HSMs in different AZs.
- The cluster replicates keys and configurations automatically.
3. Key Use Cases
- Highly Secure Key Management: Ideal for organizations with strict compliance requirements, ensuring no third-party access to encryption keys.
- Offloading Cryptographic Operations:
- Offload SSL/TLS termination from web servers for better performance.
- Enhance the efficiency of cryptographic processing.
- Database Encryption: Integrate with Oracle
Transparent Data Encryption (TDE)or other systems to securely encrypt data at rest. - Certificate Authority (CA) Protection: Secure the private keys of your CA(Certificate Authority) to maintain the integrity of your PKI.
- Custom Key Store for AWS KMS: Use CloudHSM as a custom key store for AWS KMS to combine AWS service integration with dedicated hardware security.
4. Key Differences: CloudHSM vs. AWS KMS
| Feature | CloudHSM | AWS KMS |
|---|---|---|
| Control | Full control over keys | AWS manages the keys |
| Compliance | FIPS 140-2 Level 3 certified | FIPS 140-2 Level 2 certified |
| Integration | Supports industry standard APIs | Native AWS API integration |
| Cost | Higher (dedicated appliance) | Lower (shared service) |
| Scalability | Requires manual cluster setup | Auto-scaled by AWS |
5. When to Use CloudHSM
- When you need full control over cryptographic material.
- To meet compliance mandates such as FIPS 140-2 Level 3.
- For custom integrations requiring industry-standard encryption APIs.
- To offload cryptographic processing from general-purpose servers.
6.1 Question
The chief information security officer requires that all data be encrypted at rest when stored in the cloud. The company wants complete control of the encryption key lifecycle management. The company must be able to immediately remove the key material and audit key usage independently of AWS CloudTrail. The chosen services should integrate with other storage services that will be used on AWS.
Which services satisfies these security requirements?
- A. AWS CloudHSM with the CloudHSM client
- B. AWS Key Management Service (AWS KMS) with AWS CloudHSM
- C. AWS Key Management Service (AWS KMS) with an external key material origin
- D. AWS Key Management Service (AWS KMS) with AWS managed customer master keys (CMKs)
Correct Answer: B - AWS Key Management Service (AWS KMS) with AWS CloudHSM**
Explanation: AWS KMS with AWS CloudHSM allows the company to maintain control over key material while benefiting from the integration of KMS for key management. CloudHSM provides the ability to store the encryption keys on hardware security modules (HSMs) that are managed and operated by the customer. This setup provides the ability to immediately remove key material and independently audit key usage.
Other options:
- Option A: AWS CloudHSM with the CloudHSM client provides complete control over key material, but it does not offer the same level of integration with other AWS storage services as KMS does.
- Option C: AWS KMS with an external key material origin allows the use of customer-provided keys, but it does not offer the same level of independent key auditing outside of CloudTrail.
- Option D: AWS KMS with AWS managed CMKs is a good choice for key management, but the company does not have full control over key lifecycle management as AWS manages the key material.