AWS WAF
AWS WAF is a web application firewall that helps protect web applications and APIs against common web exploits and vulnerabilities, such as SQL injection (SQLi), cross-site scripting (XSS), and HTTP flood attacks.
It operates mainly at Layer 7 (Application Layer) and allows us to create customizable rules to block, allow, or monitor web traffic based on conditions like IP addresses, HTTP headers, URI strings, and request rates.
AWS WAF works closely with AWS Shield Advanced, which provides managed DDoS protection for Layers 3–7 (Network, Transport, and Application layers) and offers 24/7 access to the AWS Shield Response Team (SRT) for faster attack mitigation.
- Use AWS WAF when we need
customizable protection against common web applicationvulnerabilities and moderate HTTP floods. - Use AWS Shield Advanced when we need
broader DDoS protection (L3-L7), financial protections (DDoS cost protection),24/7 SRT support, and automatic advanced mitigations for high-risk applications.
1. WAF integration with AWS services
AWS WAF is tightly integrated with:
- Amazon CloudFront (Global service) — Protects content delivery across the world.
- Application Load Balancer (ALB) (Regional service) — Protects HTTP/HTTPS applications in a specific AWS region.
- Amazon API Gateway(Regional service) — Protects REST and WebSocket APIs.
- AWS AppSync(Regional service) — Protects GraphQL APIs.
AWS WAF always behaves according to the scope of the associated service:
- Global when attached to CloudFront
- Regional when attached to ALB, API Gateway, or AppSync.
2. AWS WAF Rate-Based Rules
- AWS WAF offers a single "rate-based rule" feature.
- Different rules (such as
blanket application-widerules,URI-specificrules, and maliciousIP-focusedrules) are designed based on the application's needs, but technically they are all rate-based rules under the hood. - How Rate-Based Rules Work:
- Tracks the number of requests from each unique source IP address over a rolling 5-minute period.
- If a source exceeds the configured rate threshold (number of requests), AWS WAF automatically blocks further requests from that IP until the request rate drops below the threshold.
- Purpose: Provides automatic protection against HTTP flood attacks and abnormal traffic spikes with minimal operational overhead.
- Common Use Cases:
- Blanket Rule: Protects the entire application from large-scale floods.
- URI-Specific Rule: Applies stricter request limits to sensitive endpoints (e.g.,
/login,/api/checkout). - Known Malicious IP Rule: Proactively blocks traffic from IPs that have previously triggered suspicious activity.
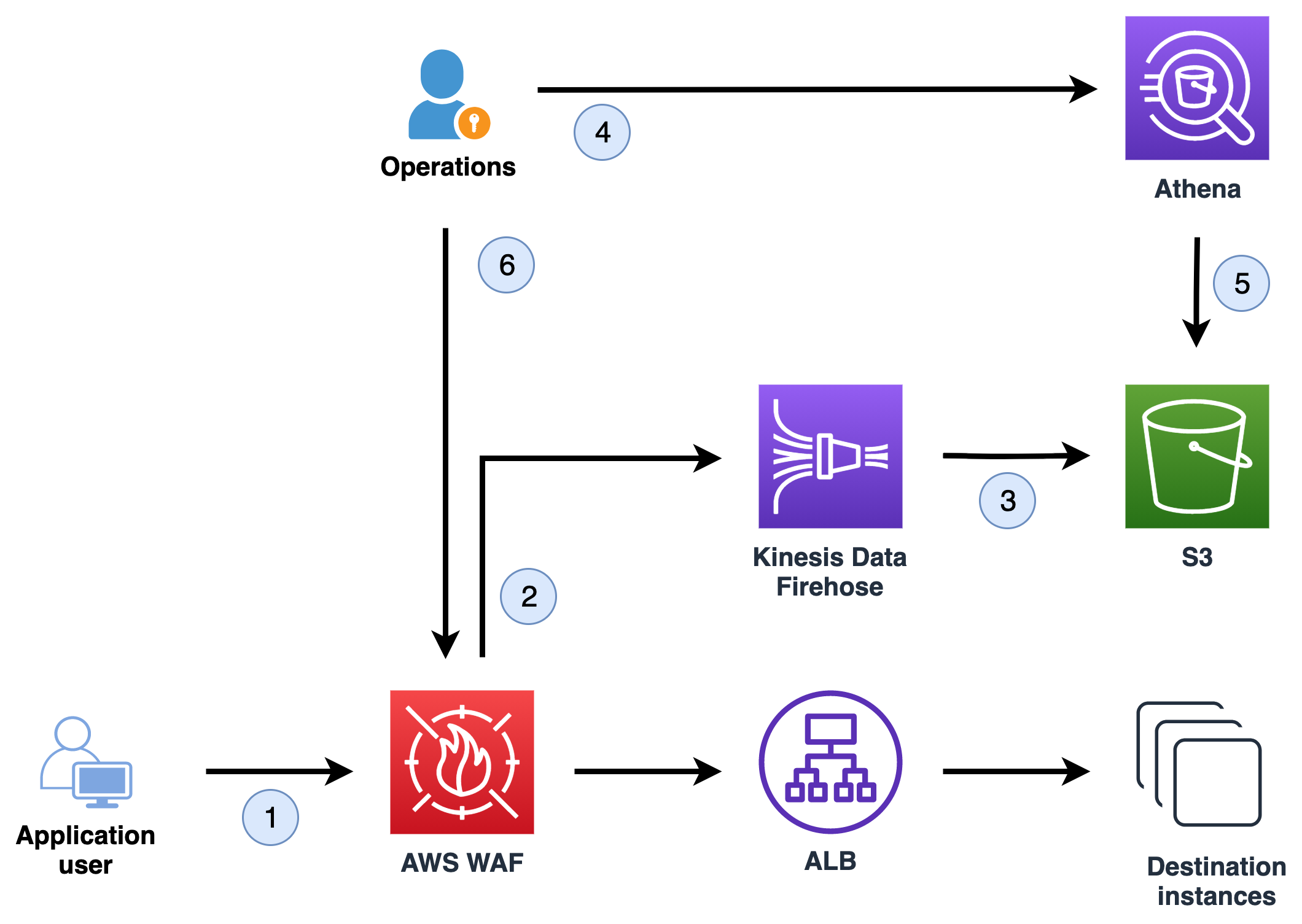
Figure 1 shows how incoming request information is captured so that the operations team can use it to determine rate-based rules.
3. Match Rule Statements to protect web applications
Geographic Match: Based on the geographic location (country, region, continent) from where the request originates.IP Set Match: Filter traffic coming from specific IP addresses or IP ranges.- Label Match: Custom match criteria based on AWS resource tags applied to incoming requests.
- Regex Match: Uses regex patterns to match specific patterns in HTTP headers, body, or URI strings.
- Regex Pattern Set: Uses multiple regex patterns in HTTP headers, body, or URI strings.
- Size Constraint: Based on the size of requests
SQL InjectionAttack: Protects against SQL injection- String Match: Filters traffic based on specific string patterns in request headers, body, or URI.
- XSS
Scripting Attack: Blocks requests that contain Cross-Site Scripting (XSS) threats.
4. Geographical filtering (country, regions, or IP addresses blocking)
- For simple, blanket restrictions by country, use the built-in Amazon CloudFront geographic restrictions feature because it is simpler to configure and has no additional cost.
- If required more granular control (e.g., specific regions within a country + allow a few IPs even inside a blocked country) or want to combine geo-blocking with other security rules(like SQL injection protection, rate limiting, etc.), use AWS WAF.
5. Handle SQL injection & Cross-site scripting
AWS WAF can detect and block requests that contain patterns typical of SQL injection attacks or cross-site scripting (XSS) attacks by using built-in managed rule groups or custom rules.
- SQL injection protection: Detects and blocks malicious SQL code intended to manipulate or compromise databases.
- Cross-site scripting (XSS) protection: Detects and blocks malicious scripts intended to be injected into web pages and executed by users' browsers.
6. AWS WAF ARN (The Identifier)
WAF ARN is the address of the WAF Web ACL (Web Access Control List), not the address of the resource it is protecting. The AWS WAF service uses the ARN to reference a specific Web ACL, which then associate with the resource that we want to protect (e.g., an Application Load Balancer, Amazon API Gateway, or Amazon CloudFront distribution).
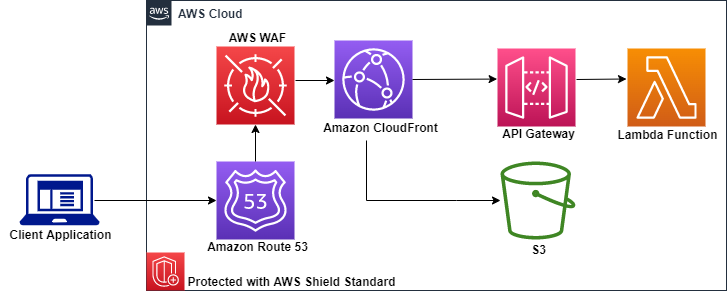
6. Question: AWS WAF and API Gateway - 2025
A financial company hosts a web application on AWS. The application uses an Amazon API Gateway Regional API endpoint to give users the ability to retrieve current stock prices. The company's security team has noticed an increase in the number of API requests. The security team is concerned that HTTP flood attacks might take the application offline.
A solutions architect must design a solution to protect the application from this type of attack.
Which solution meats these requirements with the LEAST operational overhead?
- Create an Amazon CloudFront distribution in front of the API Gateway Regional API endpoint with a maximum TTL of 24 hours
- Create a Regional AWS WAF web ACL with a rate-based rule. Associate the web ACL with the API Gateway stage. (
Correct Ans) - Use Amazon CloudWatch metrics to monitor the Count metric and alert the security team when the predefined rate is reached
- Create an Amazon CloudFront distribution with Lambda@Edge in front of the API Gateway Regional API endpoint Create an AWS Lambda function to block requests from IP addresses that exceed the predefined rate.
Explanation:
- A rate-based rule in AWS WAF automatically blocks or throttles requests when they exceed a specified threshold (like too many requests per 5 minutes).
- This is the simplest, most automatic, and least operational overhead solution to protect API Gateway from HTTP flood attacks.
- Regional WAF can be directly attached to Regional API Gateway endpoints.
Why NOT the others?
- CloudFront with TTL: Helps cache content, but doesn’t protect against request floods.
- CloudWatch alarms: Only alerts you after a flood happens; it doesn't block anything automatically.
- CloudFront + Lambda@Edge: Can block requests, but needs custom code (Lambda@Edge) = higher operational overhead.